Proper Identity Management Systems Extend Beyond The Blockchain

Improper management of identity is a fundamental reason for a lot of problems encountered in the finetech and identity management industry as a whole. This includes but is not limited to issues such as corruption, fraud, theft and several forms of graft. This weakness is exploited by taking advantage of other reasons such as system inefficiencies and deliberate dishonest human interference for personal or organisational gains.
Problems in ID management
Identities are improperly managed most of the time because the real owners lose control of their data as soon as they are submitted to the companies. Centralized management of identities and KYC data is overwhelmed with so many disadvantages and security challenges that it is becoming a subject of serious concern especially in the fintech and financial services industry.
Ideally, identity management describes the management of individual identities, their authentication, authorization, roles and privileges within or across system and enterprise boundaries with the goal of increasing security and productivity while decreasing cost, downtime, and repetitive tasks.
Most of the public data are usually stored in centralized servers with large storage capacity. Therefore, crucial information of a lot of people are held in one place. This exposes such stored data to a lot of risk. For instance, in the event of a crash, the amount of loss will be enormous, also, having a lot of valuable information in one place makes such a server a high target for hackers, and makes it more prone to attacks. This is because the rewards for a successful breach increases with the number of identities that are held in the database.
When identities are stored in a particular location, the probability of system failure is increased. This could happen as a result of natural disaster or caused by some other forces beyond the control of the administrators. For instance, servers located in the Houston area of the United States were affected during the bad whether caused by Hurricane Harvey earlier this year. Any information stored in such servers got damaged or lost permanently. This is the disadvantage of having a single point of failure. This is a key weakness when system security is considered.
Centralized identity systems are usually managed by a single party, that party then uses third-party processors to access the databases and process the data - often without sufficient safeguards and oversight – making the databases even more vulnerable to data breaches. Even if the operator is trustworthy, a centralized identity system is vulnerable through third-parties with authorized access.
The Self-Sovereign IDentity (SSID)
To protect the privacy of users and ensure proper management of identity, SelfKey implements blockchain technology and puts users at the centre of their identity management processes through a concept known as Self-Sovereign IDentity (SSID).
SelfKey is a digital identity management system that allows its users to truly own, control and manage their digital identity.
Just like people handle their important documents such as certificates and titles deeds by keeping them in a safe place until there is need to produce them or a copies of them, SelfKey allows for the handling of identities with similar attachment of importance. With SelfKey, ID attributes and documents are stored in user’s personal device, not in a SelfKey server and not in the Blockchain. Therefore, users decide what, when and with whom to securely share these ID attributes and documents and nobody has access to them without user consent, this is why it is called a Self-Sovereign IDentity. Hence, since there is no centralized database storing users’ identities, Equifax style data breaches which put 143 million US consumers' personal data at risk can be avoided.
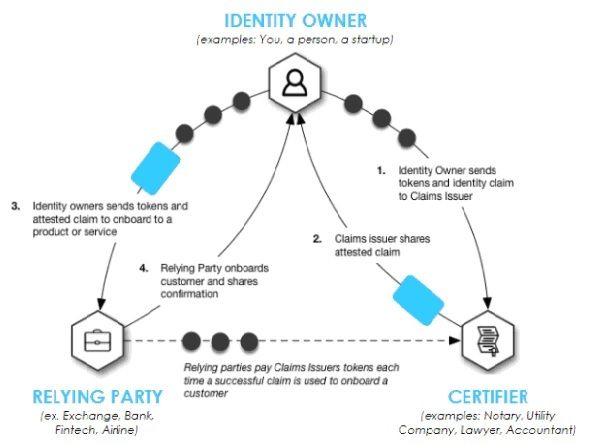
The SelfKey Network mainly comprises an Identity Wallet and Marketplace, where users can request ID documents certification and can buy products and services. Transactions are done in KEY tokens.
Also, with SelfKey, users can easily link their data between platforms whenever necessary, this will eliminate the cumbersome exercise of transferring bulky data bases or continuously repeated submission and verification of KYC information from one platform to the other especially on an international basis. It will also speed up transactions and guarantee efficiency of service while identity owners will be able to restrict the amount of their information that is publicly available at any given time.
Beyond blockchain alone
Despite being the underlying technology for the distributed decentralization and efficient management of users’ identities, blockchain alone does not solve the entire problem. This is because replicating all identity data to all parties, which is an inherent characteristic of the blockchain could potentially breach data protection laws within a specified jurisdiction. Furthermore, regulations and best practice requires that companies only store personal data that is relevant to their business—and even then, only with the customer’s consent.
Therefore, the concept of Self Sovereign Digital Identity which allows users to store their data securely in a restricted environment and make them available only when needed brings home the much needed personal control of identities.
Identity owners can now supply needed information to specific extents based on peculiar needs, KYC data can be linked for faster and efficient processing and existing corruption within the identity management ecosystem will become practically extinct.
Disclaimer. This article is paid and provided by a third-party source and should not be viewed as an endorsement by CoinIdol. Readers should do their own research before investing funds in any company. CoinIdol shall not be responsible or liable, directly or indirectly, for any damage or loss caused or alleged to be caused by or in connection with the use of or reliance on any such content, goods or services mentioned in this article.
Price
Price
Price
News
Price

(0 comments)